
James W. Meng
Home/Resume/CV -- VLNLAB -- Projects -- Abuse by the United States Government -- Writings

SLICE -- PADOLF@home -- Desktop BSD -- PLF Computing -- ReactOS z390
Since 2017, I have built several personal software & hardware projects. Some of these projects were defunct for some time but are now in various stages of construction and/or resurrection, as I transition everything to portable, cross-platform formats for the post-Intel era.
SLICE
A portable Linux container running Slic3r.
We have previously discussed the illegal theft and regulation of privately owned intellectual property by the United States government and its technology industry.
One prominent vector by which this is accomplished is in the digital fabrication sphere. Since the 3D printing boom began in the first half of the 2010s, independent manufacturers and developers of 3D printing hardware and software have been snapped up by large corporations. What was once an open ecosystem driven forward by idealistic, thoughtful semi-professionals is now viewed as a struggling revenue stream, particularly in the consumer and prosumer spaces, with applications that in some cases run counter to these companies' broader goals.
As such, there have been efforts to centralize and corrupt the ecosystem to a significant degree. Amazon, for example, maintains a superficially-large selection of parts and materials for 3D printers, yet few are quality-checked: perhaps as much as 25% or more of their product catalog in parts consists of items that are totally non-functional due to major design flaws.
The website for Slic3r, the main free and open-source client-side 3D model gcode generator available today, offered up versions for United States users for quite some time that contained malicious code permitting remote intrusion and code execution on users' computers. We are thus far unable to confirm the entity responsible for this.
Other 3D model GCode generators create similar major code-related faults. Current versions of Simplify3D, for example, no longer produce structurally-sound solid parts. This is accomplished purposefully by irregular interruptions in the volume of extruded plastic at structurally-important points in a model and is also true of several other GCode generators.
In our view, these changes may have been implemented due to a desire to regulate the printing of functional firearms, or simply to drive prototyping of physical products to specialists - yet they have stymied efforts at high-quality self-production of any 3D printed item.
While there can be no doubt that the existence of several functional proof-of-concept 3D printed firearms is potentially a worry for governments, illegal and undisclosed regulation of software is an extremely slippery slope in our view, particularly as it relates to the purposeful disabling of software that was functional at the time of sale. On this basis there is now cause for a class action lawsuit against Simplify3D by its clients, for example.
In light of the above, we built from source code a version of Slic3r with verified integrity over a Linux installation in an isolated virtual machine container. Due to intellectual property, security, and production integrity concerns, we do not recommend running any 3D model GCode generator from your primary 'bare iron' operating system installation, nor can we recommend cloud-based GCode generators such as AstroPrint. We have therefore built Slic3r LIVE entirely without software support for network connectivity.
NOTE: All work with external disks must be done via the removable media (USB, SD card, etc.) partitions that automount in the /media/ folder. These physical devices must be connected to the virtual machine container through your hypervisor.
Download Links:
Part 1: Open Virtual Appliance format (for VirtualBox, VMWare, etc)
MD5: 8c55c1e1f84050049379b44d63fa5734
Part 2: Open Virtual Appliance format (for VirtualBox, VMWare, etc)
MD5: 72f81938a2393f262f34ce4d8ee2ec33
This is a re-release of my old live USB, Slic3r LIVE, dedicated to Heinrich Reuss, an elderly German prince who is wrongfully imprisoned in Germany for allegedly "plotting a coup" against the failed German government.
PADOLF@home
A verified, live-USB Linux distribution running BOINC.
Named in honor of its creator's Jack Russell Terrier, whose name is not actually Padolf but who nevertheless as a puppy had facial markings strangely resembling Adolf Hitler's mustache, PADOLF@home is currently the only portable, live USB implementation of BOINC, the Berkeley Open Infrastructure for Network Computing, which supports a great many non-profit distributed computing projects worldwide.
Of these projects, PADOLF@home runs two of the most scientifically significant by default: the Einstein@home project, which exists to identify and document gravitational waves emitted from objects - some of which are pulsars - in the universe using data from the LIGO gravitational wave detector; and the Milkyway@home project, which exists to build a highly accurate three dimensional model of the Milky Way galaxy using data gathered by the Sloan Digital Sky Survey.
Any computer that can boot from a USB flash drive or run a virtual machine can run PADOLF@home. Do you have an extra computer lying around at home, work or school? Use its spare CPU cycles to contribute to these projects! Unlike cryptocurrency mining, which requires expensive, specialized hardware, almost any x86-based computer made within the last 15 or so years can contribute meaningfully to these important research projects using PADOLF@home.
Standard x86 and x86-64 processors are supported, as are AMD/ATI and nVidia GPUs. PADOLF@home is NOT an "amnesiac" live USB - it is a true, fully functional portable live distribution, which means you can save your progress and shut down in the middle of a work unit when booting back into your normal OS installation.
It's a funny story: shortly after PADOLF@home was first released in 2017, Andrew "Anus the Jigger" Likierman basically went insane and did everything he could to destroy it, including but not limited to hosting a conference at Oxford on my birthday in 2018 for BOINC, and then basically paying for public download mirrors for PADOLF@home to be hacked and destroyed. Then, in 2022, someone affiliated with Oxford but pretending to be from Canada built a really, really shitty version of it called BOINC OS, lacking support for GPUs and multi-core processors, and that even performs about 10-20% worse than PADOLF@home in single-core mode. I should mention, PADOLF@home is seriously fast. So fast that it'll probably run BOINC compute tasks faster in a hypervisor than on your bare iron if you're on a new version of Windows or Linux. Anyway, they illegitimately backdated BOINC OS to 2018 via corrupt people at GitHub and never updated it. I dunno what you say about that. No point to that project. So, in January 2023 I decided to re-release PADOLF@home. Higher. Faster. Stronger. PADOLF@home VERSION 3.01 - SUPERLIGHT SUPERPUP IN SPACE!
Download Links:
Open Virtual Appliance format (for VirtualBox, VMWare, etc)
MD5: 32716a34ed65869e04a59bcd232b7233
NOTE: please adjust the number of virtualized processors according to your hardware.
x86 32-bit (COMING SOON)
AMD64 (COMING SOON)
PLF Computing was born out of a need for computing that respects the needs of professionals, technically-oriented business owners, and researchers: people who need effective protection for their ideas, designs, projects, and other forms of intellectual property - from competing interests, hackers, and even governments.
Unfortunately, no major software company provides this protection today. Major software companies, such as Apple, Google, Amazon, and Microsoft, maintain their own security services to protect their own interests in intellectual property spheres, including behavior that is strategically anti-competitive in addition to cooperating closely with Western governments. This has facilitated vast theft and destruction of private intellectual property, of which the general public remains mostly unaware and to which these companies and governments are rarely if ever held accountable due to corruption in Western courts and patent agencies.
Some governments have attempted to provide a solution to this problem by creating secure variants of Linux. The United States government has built both LPS and TENS - secure, 'amnesiac' versions of Linux designed to be run from a read-only device to improve data security. Neither is likely to function or to even be downloadable in the event that the end user is already under U.S. government surveillance, and both are considered end-of-life products as of mid-2021. The Russian government supports and maintains Astra Linux. Meanwhile, the British government, in a move that might be described either as incredibly cynical or perhaps just psychopathic, has funded the development of Kali Linux - a Debian fork poorly hidden, undisclosed, on most British Ubuntu mirrors and designed not only to provide a superficial added level of security, but also to assist those who want to flout security in violation of law in order to give government agencies a bit of excitement in prosecuting otherwise-innocent college students and the like. One particularly notable case of someone who was provoked into committing such crimes by Western governments is that of Roman Seleznev.
There is also an independent project to create a 'reasonably secure operating system' called QubesOS. In principle, it offers a number of satisfactory, software-based solutions to a wide variety of theoretical attack vectors in computer security. There are two main problems with QubesOS. One is that its funding is largely provided by the United States government and several United States corporations, chiefly Google, and source code for the operating system is only available for a few of the supporting software packages built into it - not for the entire operating system. The other is that the current Linux kernel on which it is based - known as systemd - is effectively a hypervisor into which a wide variety of processes unknown and unauditable by the user can be introduced, particularly in the event of closed-source software such as QubesOS. Recent versions of Microsoft Windows are similarly insecure - in addition to maintaining an even wider range of other security holes intended to benefit Western governments and other interests.
As an interim solution, the best alternative that we could conscientiously recommend for a long time was a fork of Debian 7.11 based on the FreeBSD kernel. While not a perfect solution, it does offer greater transparency to the user as well as a far more limited opportunity for intrusions and introductions of malware. This distribution has disappeared from most Debian mirror servers. We offer download links below.
While it is true that there are several structural aspects of BSD that are superior to Linux in a security sense, the primary reason it is more secure than other alternatives in real life is simply that today, most malware and other exploits are built by Western governments and their contractors. Today's operating systems involve many levels of code abstraction; and, because that malware is more or less accessible to other parties once released 'into the wild', exploits tend not to be built for operating systems based on Unix, BSD, Solaris, etc. because these operating systems are mainly used in mission-critical server applications in major organizations. Building exploits for these operating systems that are targeted at desktop users would, therefore, be potentially quite dangerous. As a result, BSD is compelling as a potential solution for the problems we address above.
The challenge with this version is that it is not easy to install, and will only run on BIOS-based (i.e., non-UEFI) systems. Nevertheless, it can be installed in many older garden-variety PCs at the 'bare iron' level, and can even be made to work on newer systems with the assistance of a bootloader like rEFIt or rEFInd.
Download links:
Debian-kFreeBSD 7.11 (i386)
Debian-kFreeBSD 7.11 (AMD64)
PLEASE NOTE: this version of Debian is now beyond end-of-life. For people experiencing severe security and hacking difficulties, I now recommend OpenBSD or FreeBSD.
For those inclined to try out a first move to BSD, you might have a look at this excellent introductory handbook from the FreeBSD Foundation, as well as this excellent guide on setting up a graphical desktop environment under FreeBSD.
BSD is notorious for difficulty in downloading OS images. I blame corrupt/criminal security agencies and other criminals in the tech industry. To that end, torrents tend to be the easiest way to get ahold of everything. Here is a full list of FreeBSD torrents. I actively seed all of them.
PLF Computing
My defunct IT consulting firm, and the secure, proprietary office desktop I built.
I founded and ran an IT consulting company on Long Island, NY for about a year. In the process, I attempted to build a secure, proprietary office desktop around the nVidia Jetson architecture that would provide good performance along with both a small physical and electrical footprint - the PLFbox.


In so doing, I first planned to run ALT Linux, but in the end, updates to the distribution made it nearly useless for use as a desktop workstation. Granted, the Jetson Nano wasn't originally intended for use as a desktop, though it works quite well as one. But eventually Ubuntu put through a very compelling set of driver updates that allowed even more everyday processing tasks to be offloaded to the Jetson's very capable GPU in desktop use, so I returned to their distribution.
Another goal was to pull the desktop out of the Wintel cesspool entirely, chiefly to protect clients from some of the criminals operating out of Western tech majors like Microsoft, Google, and Apple - as well as from the American NSA. And not just with the Jetson Nano, but with an alternate networking solution also (the Jetson, by default, was only compatible with Intel WiFi hardware). Work on porting Realtek drivers to the Jetson system began, but never finished before it became clear there was no way to really get away with offering such a product in Western markets. I would have been run out of business entirely.
But, as it often does, the free market stepped in to fill the gap I had identified, and the Raspberry Pi Foundation released the Raspberry Pi 400 not long thereafter in fall 2020. Apple likewise began introducing new computers with an ARM-based processor shortly thereafter. It's not a trivial matter - you can do the same fundamental tasks on an ARM-based system with 10 watts that an Intel-based system needs 500 watts for. That's why I don't feel the least bit bothered that Apple and the Raspberry Pi Foundation were the first with a mass-market ARM PC resurgence. The entirety of Planet Earth will be vastly better off running on the ARM architecture in a lot of ways. It is a big help in tackling carbon output driven by electricity consumption, for example.
Beyond that, and in addition to consulting on various novel special projects, we provided quite a lot of setup, support, and e-waste services. Eventually, my favorite local scrap metal dealer, Gershow Recycling, got into the e-waste business, saving me the trouble of doing the processing work myself and getting customers paid for their e-waste besides. Prior to my arrival, New York was a place where e-waste could only be disposed of at scale with considerable difficulty - it was really fantastic to have been able to make such a positive environmental impact.
I still do IT consulting work on a project basis, though no longer on-site. Call or e-mail me to discuss.
PLEASE NOTE: since this was written, the Linux ecosystem has continued to devolve into a cesspool not unlike that of Microsoft and Intel. Because the Jetson Nano effectively only runs Ubuntu Linux, I no longer recommend or use it, even though it is still really great hardware. Instead, I now recommend the Raspberry Pi series or, for those needing more power, the PINE64 series, as these are well integrated with the BSD ecosystem already.
The IBM z390 emulator in a ReactOS virtual machine.
Recently while taking a course on IBM mainframe assembler language, I needed to run the above emulator - but I didn't want to buy a PC, or pay for Windows. More on that in a bit, but first, a joke:
***
Three Microsoft programmers and three IBM programmers are traveling by train to a conference. At the station, the three IBM programmers each buy tickets and watch as the three Microsoft programmers buy only a single ticket.
"How are three people going to travel on only one ticket?" asks one of the IBM programmers.
"Watch and you'll see," answers the Microsoft programmer.
They all board the train. The IBM programmers take their respective seats but all three Microsoft programmers cram into a restroom and close the door behind them.
Shortly after the train has departed, the conductor comes around collecting tickets. He knocks on the restroom door and says, "ticket, please." The door opens just a crack and a single arm emerges with a ticket in hand. The conductor takes it and moves on.
The IBM programmers witness all this and agreed it was quite a clever idea. So after the conference, the IBMers decide to copy the Microsofties on the return trip and save some money.
When they get to the station, they buy a single ticket for the return trip. To their astonishment, the Microsoft programmers don't buy a ticket at all.
"How are you going to travel without a ticket?" asks one of the perplexed IBM programmers.
"Watch and you'll see," answers one of the Microsoft programmers.
When they board the train the three IBM programmers cram into the first restroom they can. The three Microsoft programmers pile into another one nearby. Shortly thereafter, the train leaves the station.
After a brief interval, one of the Microsoft software engineers leaves his restroom and walks over to the restroom where the IBM programmers are hiding. He knocks on the door and says, "Ticket, please..."
***
This emulator is not really written for Windows. It's mostly written in Java. At the same time, it's challenging to set up on ReactOS because ReactOS still hasn't had environment variables implemented throughout the whole MS-DOS compatibility layer, which is required because the scripts that run the various Java apps that carry out the emulator's functions are in DOS batch file format. And this is why I packaged it as a virtual machine: so you can run this image on a Mac, on Linux, on BSD, on a Chromebook, even on your phone if you want. There's no need to have anything to do with Microsoft to program an IBM mainframe at all.
Open Virtual Appliance format (for VirtualBox, VMWare, etc)
MD5: 3ecac4ebbf3782fe4494128296772b3b
NOTE: Windows SmartScreen sometimes incorrectly reports that this package contains malware and/or a trojan horse sort of virus. This is NOT true:
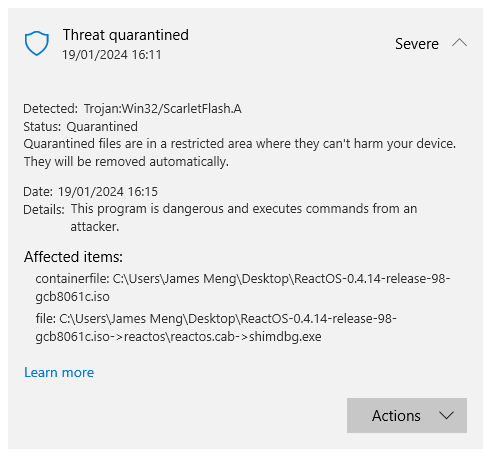
Sadly, Microsoft is well known for their criminal anti-competitive behavior already, and this is just the latest example. But if you're still worried and want to verify this for yourself, you can browse the code of the file they flagged here. And you'll see - no malicious code at all. Google Drive incorrectly flagged me for this as well. What I'd be worried about is - you may experience issues from Microsoft and/or criminal western security types hacking you to teach you a lesson if you use ReactOS. And I unfortunately can't do anything about that. You just have to be aware and ready to report them to law enforcement in your country if the issue arises.